Meet IdAux — The Architects of Digital Trust
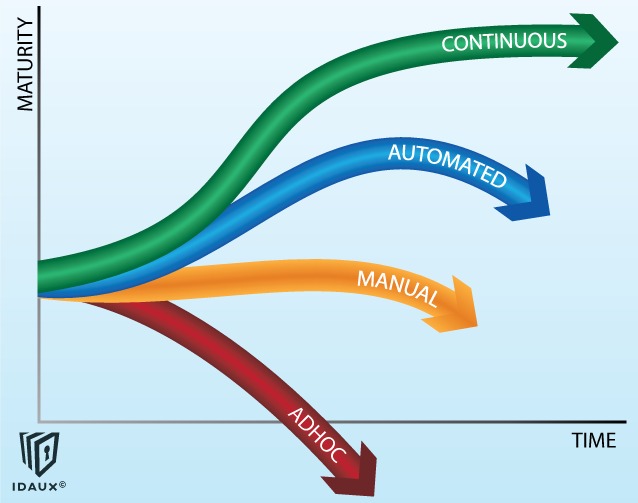
At IdAux, we don’t just build cybersecurity systems — we build digital trust. In a hyperconnected world, where threats are constant and perimeters no longer exist, our mission is simple: Make Value-Based Zero Trust the standard, not the exception.
Our Vision
To reshape the future of digital security by empowering businesses to operate fearlessly, without assumptions — protected by intelligent, adaptive, and identity-first defense.
We believe that trust should be earned, verified, and continually reinforced — not assumed. That’s why IdAux was founded: to bring clarity, control, and confidence to modern organizations navigating a complex threat landscape.
Who We Serve
From Fortune 500 companies to cloud-native startups, we serve security-conscious organizations across industries:
Private enterprise:
- Finance
- Healthcare
- Retail
- Manufacturing
- Energy
Public enterprise:
- Federal Government
- State Government
- Local and Tribal
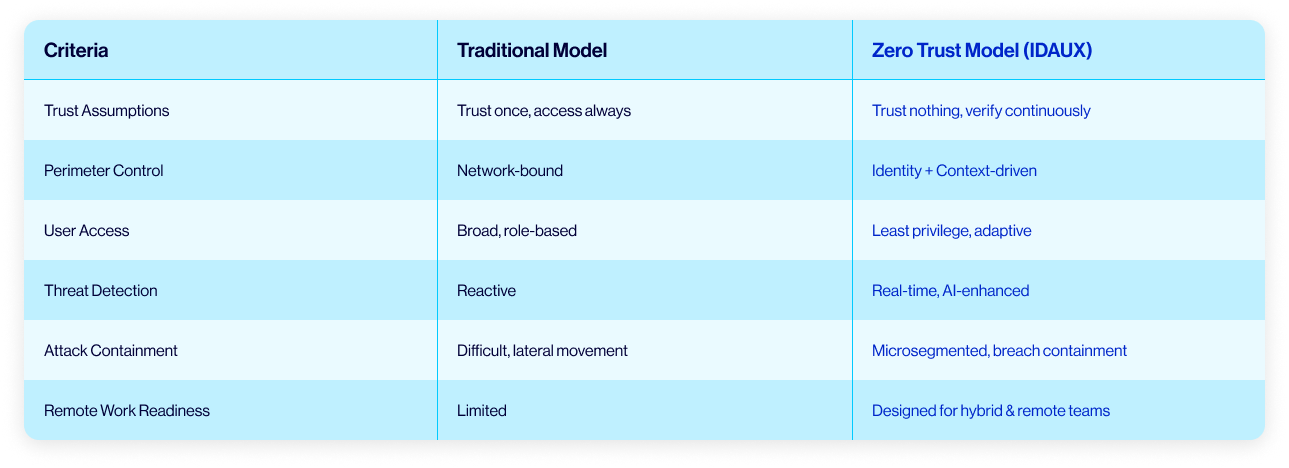
Comprehensive Value-Based Zero Trust Solutions, Built by IdAux
Whether you're securing a hybrid workforce, modernizing infrastructure, or protecting sensitive data across multi-cloud environments, IDAUX delivers Zero Trust solutions designed for scale, speed, and resilience.

Offerings

1. Identity and Access Management Strategy & Execution
Ensure only the right users have the right access at the right time — with adaptive, context-aware controls.

MFA

SSO

Role-Based Access

Conditional Access

2. Micro-segmentation and Breach Containment
Reduce attack surface and limit lateral movement by segmenting workloads, enforcing granular policies, and isolating threats instantly.

Workload Isolation

Policy-Based Enforcement

ZTNA

3. Data Governance and Management
Protect sensitive data through enterprise-grade governance, ensuring security, compliance, and lifecycle management across the organization.
Data Lifecycle Oversight

Encryption & Key Management

DLP
4. Intelligent Micro-segmentation for Breach Containment
Divide your network into secured segments to limit lateral movement and isolate potential breaches instantly.

Workload Isolation

Policy-Based Enforcement

5. Cloud Security Posture Management (CSPM)
Proactively identify and fix misconfigurations, compliance gaps, and vulnerabilities across your cloud infrastructure.

Multi-Cloud Coverage

Compliance Mapping

Real-Time Scanning

6. End-to-End Data Protection & Enterprise-Grade Encryption
Safeguard sensitive information at every touchpoint with full-spectrum encryption and secure data governance.
Encryption In-Transit & At-Rest

DLP

Key Management
No matter where your data lives or how your teams work — IDAUX provides Zero Trust solutions that adapt, scale, and evolve with your business.
Explore the Full Solution SuiteIdAux Aligns with the World’s Most Rigorous Security Frameworks
IdAux is committed to helping organizations meet — and exceed — the world’s most demanding cybersecurity and compliance standards. From financial institutions to healthcare providers and public-sector agencies, we provide the foundation for operational trust and regulatory peace of mind.
Our Certifications & Frameworks

SOC 2 Type II
Third-party attested controls for security, availability, and confidentiality — built for enterprise trust.

ISO/IEC 27001
Certified information security management system (ISMS) to manage data risks across global operations.

GDPR Ready
Data privacy aligned with EU General Data Protection Regulation for processing and protecting user information.

HIPAA Compliant
Designed to safeguard Protected Health Information (PHI) in alignment with U.S. healthcare regulations.

NIST 800-207 Aligned
Fully aligned with the National Institute of Standards and Technology’s Value-Based Zero Trust architecture principles.

CSA STAR Registered
Cloud Security Alliance–recognized for transparency, governance, and best-in-class cloud security practices.